Choose what protection you need

Your security and/or encryption methods will only be effective if each level of your system is secure. You can send your emails with unbreakable encryption, or use the strongest conceivable passwords, but if your system is hacked, or otherwise vulnerable, your efforts may be futile, as your encryption can be circumvented without any need to break it. Depending on your risk level and the sophistication of your adversary, protection strategies range from simply keeping your laptop or phone on you at all times, to using a second-hand, cash-bought, laptop and practising robust InfoSec, during a specific project.
Think of ‘protecting your system’ as building a house of cards – for it to work, you must build your security from the bottom up. In this chapter, you will learn how to build the foundations of a secure system by managing the security of your hardware and firmware.
You decide
This chapter is the most important of the book. It is also fairly technical, and contains the most challenging information of any chapter in the book. The solutions here are many, but ultimate security is the outcome of only one. Here, we lay out the horrible reality of the extent of hardware vulnerabilities, and leave you to decide what the appropriate security measures are for yourself. For several of the solutions described here (such as specialist modifications to hardware, and the replacement of firmware) you will need expert help.
As lengthy and technical as much of this chapter is, please do read on! You should be aware of the vulnerabilities within your own system, even if you do not have the ability or need to currently solve them. This is important information that will guide your trust and use of your system, and prepare you for the future, simpler solutions that we hope will soon be developed.
GYour computermodel
Definitions
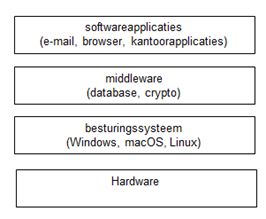
- Interface - screen
- Applications - your software/programs
- Middleware - programming that "glues together"/mediates between two separate and often already existing programs: e.g. allows programs to access databases
- Operating System – Windows XP/7/8/10, Mac OS X, Linux, etc.
- Firmware – fundamental software programmed onto hardware that provides instructions for how the device communicates with the other computer hardware
- Hardware – the physical elements that comprise a computer system
In this chapter, we will primarily consider security at the most fundamental level: hardware and firmware.
Hardware and firmware
We will explain how to obtain safe hardware and how to keep it safe. You only need to choose what risk level suits your needs and take the corresponding appropriate steps.

Laptops
‘Hardware’ refers to your physical machine. Desktop computers are not recommended for important journalistic work as they are immobile and as such not only impractical, but vulnerable to physical intervention when you are not around. Laptops will be discussed here. For our purposes, ‘laptop’ refers to all physical components, including the battery, hard disk drive, CD drive, Wi-Fi card, microphone, and webcam. Let’s also consider additional hardware: any keyboard, mouse, scanner/printer, webcam, and so on that you connect to your laptop.
Threats to hardware may be:
- Theft or damage
- Physical attack
- Virtual/remote attack
The main risks to your hardware are that it will be stolen, damaged, physically tampered with or ‘bugged’; or virtually/remotely accessed in order to transmit signals (i.e. collect and deposit your information).
Five key measures are important for hardware protection:
Preventing virtual and physical attacks on your hardware
- Buying the right laptop
- Modifying your hardware
Preventing physical attacks on your hardware
- Buying your laptop anonymously
- Guarding your laptop
- Detectability measures (should you be separated from your laptop)
Although these five steps may sound confusing and even daunting at first, they are all entirely doable for journalists who are new to I.T. and InfoSec. How to obtain and maintain your secure hardware is explained in this chapter – all you have to do is choose the risk level you want to prepare yourself for, and take the appropriate steps.
Preventing virtual and physical attacks on your hardware
Buying the right laptop, suited to your risk level
What laptop you buy determines the security level you will be able to achieve. As we learn more about extensive surveillance capabilities from the Snowden documents, we learn too what machines are and are not securable. Hopefully, with time, we will be able to develop more secure solutions. However, at the moment, very few laptops are entirely securable against the greatest threats.
This may not be a problem for you or your source, depending on who your adversary is. If you are defending your communications and data from a powerful government or an ally (which, in practical terms, may include significant banks and corporations), you will need excellent security for your laptop/s. Otherwise, whether you are defending against corporations, political, military, terrorist or rebel groups, private security firms, or specific individuals, you will have to estimate how sophisticated the tools of your adversary are; how easy those tools would be to employ against you; how important you are as a target; and thus, what measures you wish to take.
There are four issues to consider when buying a laptop that determine the securability of your system.
Hardware maintenance
You may wish to have a laptop that allows you to unscrew the casing and get inside the machine, so you can do some basic hardware ‘maintenance’, and choose which components to keep or disable. Many IBM/Lenovo, HP, and Dell laptops are suitable for this, and provide extensive hardware documentation on their websites that assists with DIY hardware modification.[1].
You cannot easily open the casing of MacBooks – this requires some skill and even so, performing your own hardware maintenance on a MacBook may void its warranty.
Firmware
Firmware is the software programmed onto your laptop’s hardware at a deep, foundational level. In basic terms, firmware provides instructions for how parts of your laptop should communicate with each other. Firmware is another possible attack point, as highly sophisticated hackers (likely state-level) may be able to remotely access it and gain privileged control over your machine. This could undermine your subsequent security efforts.
You can ‘lock’ your firmware on a MacBook, making your firmware accessible only via a password that you set for it. The ability to lock firmware on a Mac provides a specific security advantage over other laptops, of which only a limited number of models can be secured by the highly technical, specialist task of replacing closed source firmware (whereby the code is privately owned and not publicly available or auditable) with open source firmware (called ‘Coreboot’, which is free to all and has publicly available and auditable code). Of course, confidence in the security provided by the MacBook ‘lock’ depends on one’s trust for Apple. Likewise, confidence in Coreboot depends on one’s trust for the auditors of the code. However, the Mac firmware lock has no known vulnerabilities, and using it could make a hack more effortful.
The Mac Firmware Lock: this is such an easy function to use on Mac, and one that provides considerable defence against firmware hacks. Therefore, Mac users at various risk levels may wish to use this. To set a firmware lock on your Mac (OS X), boot the machine up, holding down ‘cmd’ and ‘R’ keys as it boots to enter Recovery mode. On the top menu bar, go to ‘Utilities’ > ‘Firmware Password Utility’ > ‘Turn On Firmware Password’. Choose a strong password (see chapter 8) and click ‘Set Password’. It is very important that you remember this password, or you may lose access to your Mac.
Chipsets
From around 2006, Intel started putting special components in their chipsets (combinations of chips that work together on laptop motherboards) to allow the automated management of systems over a network. This is called ‘Intel Active Management Technology’, and means that an I.T. technician in a large office/university I.T. suite can update software, or do other things to machines, without having to be physically near them. The problem, of course, is that the same functionality can be abused to install spyware or manipulate the systems in other ways. All laptops made after 2008 contain these chipsets, and are therefore vulnerable to these types of attacks when they are on a network.
The ‘Intel 945’ chipset is the most recently made chipset without this automatable feature, and hence lends itself to a securable motherboard/computer. When choosing a laptop, you can see what its chipset is on the specification.
Operating system
You may also wish to buy a laptop that allows you to install the operating system of your choice (ideally, open source, whereby the source code is publicly available). You can do this fairly easily on most laptops, except MacBooks, where it is a bit more tricky.
You can either totally wipe a pre-installed operating system and install a new one, or you can use ‘virtual machines’ or ‘sandboxes’ on your pre-installed operating system, essentially running multiple operating systems at once. Proprietary operating systems (Windows, Mac) are closed source and may have various inbuilt security backdoors, intentional or otherwise – so it is not known how much security simultaneously running alternate operating systems actually provides. Whilst most laptops allow users to easily wipe their Windows operating system, wiping a MacBook of its operating system is inadvisable as it may compromise the system’s overall functioning.
It is possible to use various operating systems on Mac, but this requires knowledge of how to run a ‘virtual machine’,, which we won’t go into here for the reasons set out above. Alternatively, you can use the operating system Tails on a Mac, which bypasses the hard drive and runs from a USB drive (see Chapter 2). How can you interpret these four fundamental security issues for your own threat modelling? Remote hardware, firmware and chipset accessibilities are likely to be possible only by the intelligence agencies of technologically advanced and wealthy nations – but all technology tends to be democratised to less powerful groups over time. Therefore, if could potentially list such an intelligence agency as an adversary, you may wish to consider those three vulnerability factors. Even if you do not face such a risk level, you may wish to take some security precautions as a safe measure nevertheless (particularly those that require little effort, such as locking firmware on a Mac).
Risk level suggestions (threat modelling)
It is likely that technologically advanced intelligence agencies have access to backdoors in operating systems. However, it may also be the case that especially large or powerful corporations can obtain such knowledge or access too – so if your adversary is a corporate giant, you should consider the security implications of your operating system.
Choosing what laptop to use is not easy – you should take your time processing this information, assessing your risk levels, and deciding how much effort and discipline you will invest into your information security.
Here are some suggestions of what laptops you could buy at various generalized risk levels:
- low risksdragnet surveillance, low grade individual hacking, theft | You can start with any laptop. A good investigative journalist will outgrow this category before long! Most systems are fairly securable against unsophisticated threats at the software level. By keeping your machine on you at all times, you can defend against theft or physical interventions. You can also avoid the digital dragnet through software and application choices.
- medium risk: targeted surveillance, by an adversary who is prepared or able to invest relatively limited resources | Use either a laptop on which you can wipe the current operating system and install your own (ideally, an open source Linux operating system); or use the Tails operating system for project work from any computer. See chapter 2 for more information on operating systems.
- high risk: targeted surveillance by an intelligence agency There are only a handful of machines that can be confidently secured against remote hardware, firmware and chipset accessibility. Currently, the model that is being most frequently secured in this way is the IBM ThinkPad X60 (and X60s). It has an Intel 945 chipset (i.e. pre-AMT), and specialist work can be done to secure the hardware and firmware (the proprietary firmware can be replaced by open source firmware, ‘coreboot’). You should then use the Tails operating system (see chapter 2) on this secure machine, to maintain system security.
- If you require one of these secure machines, please safely make contact with us at the Centre for Investigative Journalism. You can send an encrypted email to infosec@tcij.org or contact the office (http://www.tcij.org/about-cij/contact-cij). infosec@tcij.org of contact opnemen met het kantoor (https://www.tcij.org/about-cij/contact-cijIf you want to do-it-yourself, you could buy a laptop with a pre-AMT chipset that allows you to open the casing, and use online documentation for the laptop to guide you through some basic hardware maintenance. For instance, you could remove your laptop’s hard disk drive, and remove/disable your laptop’s microphone, webcam, Wi-Fi card, Bluetooth card, or 3G modem, and Ethernet port (see point 2 in this chapter). However, unless you have been specifically trained, you will be unable to do the more minute hardware modifications for top security, or to replace the firmware.
- Top risk level: targeted, directed surveillance by an intelligence agency | In very high-risk situations, you should have at least two laptops that have all the above security measures implemented – only, one of those laptops must never connect to the internet by any means. This will be your ‘airgapped’ machine – a laptop that never, ever goes online. This can be a very useful machine for storing or accessing files (for example, that you may have on a USB stick), writing articles, and producing your reports on. You, or the specialist helping you, should remove or disable all of the laptop’s connectivity devices, to ensure it is truly offline at all times (see point 2). Ideally, both your airgapped and your online machine should be two specially secured IBM ThinkPad X60s.
Fact: Glenn Greenwald uses an airgapped laptop to work on the Snowden documents.
The airgap adds an extra level of security to your/your source’s data, because your important documents are stored not only on a secure machine, but also entirely offline. Even the most secure machine may be exposed to some degree of risk when it goes online – particularly if the user is the subject of a directed attack.
Modifying your hardwaree
Let’s take a look at all of the modifiable internal components that could potentially be used to surveil you, your source and your work. In Dutch some tips of Arjen Kamphuis - Bright TV
We will discuss:
- webcam
- microphone
- hard disk drive
- Wi-Fi card
- bluetooth card
- 3/4G-modem
- ethernet port
Webcam
Not only can webcams be remotely and covertly activated for specific targets, but webcam images have also been intercepted as part of dragnet surveillance programs (see the Snowden revelation of GCHQ’s OPTIC NERVE program). A simple solution is to place a sticker over your webcam. Snowden revelation of GCHQ’s OPTIC NERVE program). Een eenvoudige oplossing: plak een sticker of webcamcover over je webcam.
Microphone
Your laptop’s microphone can also be remotely and covertly activated, to capture audio. You could try putting hot glue over the microphone input on your laptop casing, to muffle sounds. Better still, open your casing and cut the microphone wire.
Hard disk drive
Some hard disk drives have been found to contain ‘bad’ firmware – that is, they could potentially be activated to compromise your security, should you become a target to an agency with a very sophisticated toolkit.
At high-risk levels, it is advisable to remove the hard disk drive and instead work from USB drives. USB drives are also ideal for storing the highly secure operating system, Tails (see chapter 2) – that is, they can hold a small, anonymising system for you to work from. USB sticks are highly portable, replicable (to share with colleagues/sources), and are easily protectable by high-grade encryption (see chapter 4). This also means that, if your laptop is stolen or damaged, the data stored on your USB is still safe. However, you may wish to keep the hard disk drive for your general day-to-day work, and work from USB drives or Tails sticks for specific projects.
Wi-Fi card, Bluetooth card, 3/4G modem
At high-risk levels, any element that permits connectivity could be remotely and covertly activated to install surveillance tools, or indeed to send your data back to an adversary. Therefore, you should aim to have as much control over your laptop’s connectivity as possible.
The best way to do this is to physically remove connectivity components. This means opening the laptop casing, and unscrewing the Wi-Fi card, as well as any Bluetooth card and 3G modem if your laptop has these (consult your laptop’s handbook if you are unsure – copies can often be found online). This may feel like a daunting task at first, but anyone with a steady hand and correct instruction can easily do this first-time.
Then you can control when you are online and offline. You could buy a Wi-Fi USB adapter, which functions in the same way as your Wi-Fi card – it allows you to connect to the internet. The difference is, that you can easily connect and disconnect the adapter from the USB port, and so you decide when you go online and offline. Alternatively, you could choose when to go online via an Ethernet cable.
Ethernet port
The Ethernet port is what you use to physically connect to a ‘local area network’ (LAN), which can be the anything from a network in a large office building or a home router box from your internet provider. Of course, Wi-Fi is now much more commonly used than wired Ethernet connections.
It is known that Ethernet ports have specific security vulnerabilities that can be exploited against especially high-risk targets. If you wish to defend your machine against Ethernet exploitation (e.g. for an airgapped machine), you could fill the port with hot glue. Alternatively, you could disconnect the port wiring inside the laptop.
Preventing physical attacks on your hardware
Buying your laptop anonymously
As you learn about InfoSec, you may wish to purchase one or two new laptops. This is not only a wise decision when working with a new high-risk source, or when working on a very sensitive project, but to prepare yourself for the possibility of such eventualities, and to implement your new InfoSec learning. The process of buying secure laptops should be as anonymous as possible in high-risk situations to prevent an adversary from pre-positioning surveillance tools in your hardware; being alerted to your new hardware and thus being motivated to physically or virtually invade your machine after purchase; or tracing your laptop/data back to you and/or your source.
The risk level of your source = your risk level
If you are working with a high-risk source, such as an intelligence whistleblower, that person may already be under surveillance. You should assume that the surveillance risk that applies to your source could also apply to you.
Anonymous purchase
The Snowden documents revealed that intelligence agencies intercept devices such as laptops, phones and other electronics, to implant surveillance tools before factory sealing them and putting them back into transit – so you should avoid purchasing any hardware (even chargers) online. Most elements of hardware can be modified to act as surveillance tools.
You should decide what model of laptop you want to buy first (after reading this chapter), and be sure to do any research before buying using the anonymous Tor browser (see chapter 3). To be safe, you can buy your laptop/s in person, with cash. If you are buying an older model you may wish to find an area, preferably some distance from where you normally shop, with several second hand electronics shops. At higher risk levels, you may wish to use several different shops to buy each laptop and accessory (e.g. USB sticks), and whilst shopping, place any device that could track you (i.e. your phone) in a Faraday cage (a metallic enclosure that prevents signal transmission) or leave it somewhere safe at home.
For media and campaign organisations, it is a good idea to pre-emptively tool up with pre-prepared secure equipment (that should be stored in a safe until use) and to train several employees in how to use it. For advice on ready-made toolkits and training, contact infosec@tcij.org. infosec@tcij.org.
Guarding your laptop
Preventing theft, damage (intentional or not), and physical attacks on your hardware, if you deem yourself to be at risk of targeted surveillance, means adopting an important new behaviour: keeping your laptop on you, near you, or within your sight at all times. Adopting such behaviour is sometimes called ‘OpSec’, or ‘Operational Security’.
If at any point your laptop is left unattended (for example, at home, in a café, or at the office) or is in someone else’s possession (for example, checked-in baggage on a flight; or being held by the police/authorities), you should consider, depending on your risk level, the possibility that the system may no longer be secure.
In Azerbedjan I once entered my hotel room and there was a man behind my laptop. He did not even flinch. Stood up, took his USB stick and apologised and left. Shameless.
Olaf Koens, investigative reporter, 21th February 2019 on Twitter
Keep your secure system as simple, small, and light as possible – avoid connecting the laptop with a mouse, keyboard, printer, docking station, or other devices (which, for high-risk targets, could conceivably be ‘bugged’) to limit the hardware you need to carry with you or be responsible for.
You need to consider the physical security of your hardware not only presently and in the future, but also retrospectively. Could it have been physically attacked before? How was it manufactured – could the hardware already be compromised?
Since we know that shipment may be a risk, we discussed buying new hardware in person, with cash. Not only is this a more anonymous way of acquiring a new laptop, but you can take physical responsibility for it immediately.
Detectability measures
Detecting possible physical interventions with your laptop is extremely difficult. If you do need to securely store your laptop for some reason (for example, if you wish to cross a country’s border without your laptop) you should try to do so in a way whereby any security breach would be detectable. Be creative - but it will be a challenge to outsmart a sophisticated adversary. Ideally, you will leave it under the close protection of someone you trust, if you cannot guard it yourself.
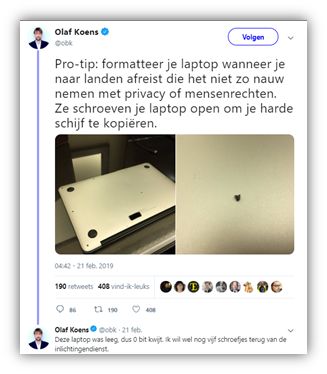
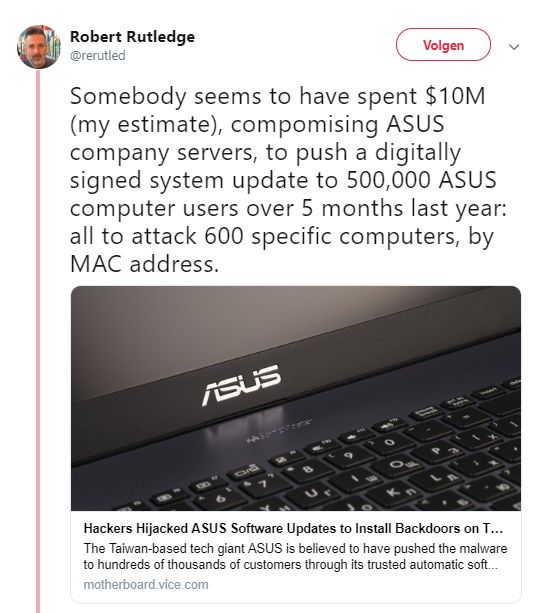
Snowden developed the appHavenin 2017 that you can use for OpSec. Be creative, but it will prove to be a challenge to be smarter than a capable adversary. Sometimes it is even clear you laptop has been compromised (by missing or damaged screws for example). Sometimes it is obvious your laptop has been compromised als Olaf Koens showed in a tweet in February 2019. He is still missing five screws.
For technological defence against low levels of risk, and as a general safety measure, you could download an open source application called Prey: Prey This is tracking software that helps users find, lock and recover their computers. It also enables you to take screenshots of the stolen laptop’s screen, and to activate the webcam to take a photo of its new owner. Downloading tracking software may feel counter-intuitive for a journalist who wants to strictly defend their privacy! Since the application is open source, it is thought to be fairly trustworthy. However, a sophisticated adversary will not be caught out by it. It is only recommended that you use this application as a defence against less advanced adversaries.
If you wish to continue using non-securable hardware, there are still measures you can take to protect you data and communications from less intrusive surveillance activities – so do read on. Just be aware that, if you become a surveillance target of someone with the resources, ability, and motivation to obtain your data, it is a fait accompli.
[1] Such hardware flexibility and documentation is also available for other brands – the above suggestions are not endorsements of these brands or their products